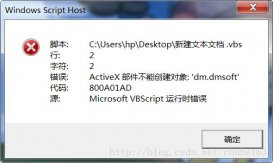
第一:依靠135端口,用wmi。像下边的脚本是得到共享目录ttt的物理目录。
strPath ="\\192.168.1.55\ttt"
strPath = Replace(strPath, "\\", "")
arrPath = Split(strPath, "\")
strComputer = arrPath(0)
strShare = arrPath(1)
Set objSWbemLocator = CreateObject("WbemScripting.SWbemLocator")
Set objWMIService =objSWbemLocator.ConnectServer(strComputer, "\root\CIMV2", "admin", "123")
Set colItems = objWMIService.ExecQuery _
("Select * From Win32_Share Where Name = '" & strShare & "'")
For Each objItem in colItems
Wscript.Echo objItem.Path
Next
/*********************************微软的脚本有问题,只能得到本机***********************************************/
strPath = "\\atl-fs-01\public"
strPath = Replace(strPath, "\\", "")
arrPath = Split(strPath, "\")
strComputer = arrPath(0)
strShare = arrPath(1)
Set objWMIService = GetObject("winmgmts:\\" & strComputer & "\root\cimv2")
Set colItems = objWMIService.ExecQuery _
("Select * From Win32_Share Where Name = '" & strShare & "'")
For Each objItem in colItems
Wscript.Echo objItem.Path
Next
/*********************************微软的脚本有问题,只能得到本机***********************************************/
第二、依靠445端口,靠smb。bt5下的 nmap
root@bt:~# nmap --script smb-enum-shares --script-args=smbuser=administrator,smbpass=toor 192.168.1.108 -p445
Starting Nmap 5.59BETA1 ( http://nmap.org ) at 2012-02-14 15:29 CST
Nmap scan report for 192.168.1.108
Host is up (0.00013s latency).
PORT STATE SERVICE
445/tcp open microsoft-ds
MAC Address: 00:0C:29:B3:F6:79 (VMware)
Host script results:
| smb-enum-shares:
| ADMIN$
| Type: STYPE_DISKTREE_HIDDEN
| Comment: Remote Admin
| Users: 0, Max: <unlimited>
| Path: C:\WINDOWS
| Anonymous access: <none>
| Current user ('administrator') access: READ/WRITE
| C$
| Type: STYPE_DISKTREE_HIDDEN
| Comment: Default share
| Users: 0, Max: <unlimited>
| Path: C:\
| Anonymous access: <none>
| Current user ('administrator') access: READ/WRITE
| IPC$
| Type: STYPE_IPC_HIDDEN
| Comment: Remote IPC
| Users: 1, Max: <unlimited>
| Path:
| Anonymous access: READ <not a file share>
| Current user ('administrator') access: READ <not a file share>
| NETLOGON
| Type: STYPE_DISKTREE
| Comment: Logon server share
| Users: 0, Max: <unlimited>
| Path: C:\WINDOWS\SYSVOL\sysvol\haiyangtop.com\SCRIPTS
| Anonymous access: <none>
| Current user ('administrator') access: READ/WRITE
| SYSVOL
| Type: STYPE_DISKTREE
| Comment: Logon server share
| Users: 0, Max: <unlimited>
| Path: C:\WINDOWS\SYSVOL\sysvol
| Anonymous access: <none>
| Current user ('administrator') access: READ/WRITE
| ttt
| Type: STYPE_DISKTREE
| Comment:
| Users: 0, Max: <unlimited>
| Path: c:\sharettt
| Anonymous access: <none>
|_ Current user ('administrator') access: READ
Nmap done: 1 IP address (1 host up) scanned in 0.56 seconds
root@bt:~#